9 Signs Your Security Awareness Training is Failing
In this article, I’ll show you why the modern approach to Security Awareness Training & Education (SATE) is failing and explain how we can do it better.
Like most things that might initially seem impossible, it all begins with a proper mindset. There’s an old saying that goes something like this: “Whether you think you can, or you think you can’t, either way you’re right”.
But if this maxim proves true across all industries and cultures, why do we throw our hands up at the thought of properly training users and say “Well, you can’t patch stupid!”?
The only guaranteed way to fail is to say “I can’t”.
Addressing the User Problem
Experienced attackers know that if they want access to a “secure” network all they need to find is the low hanging fruit. An organization’s users often represent the lowest hanging fruit because targeting users allows an attacker to bypass almost ALL security controls. All the attacker has to do is inherit user privileges to gain access to the network and then they are free to cause as much damage as possible.
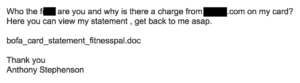
Enterprises are not properly addressing their user risk, and because of this, it’s a wide open gap in most security departments. Does your organization approach network security like this character from Lemony Snicket’s Series of Unfortunate Events?

If you don’t properly address your user problem, this is exactly what your security looks like. Attackers know that they can always bypass security controls by targeting the weakest link…your users. Even the most sophisticated digital security perimeter puts the attacker in the DMZ, but the attacker wants to be in the user land where the data resides and where the security controls are a lot less likely to catch said attacker.
The truth is that human error is the ultimate root cause of every cyber incident. So if we can do better with human decision-making, we can do better with security.
But how?
Investing in Your Users
The answer lies in investing in your users. But I’m willing to admit that securing users is not easy to implement. It takes a dedicated effort of time and money (or both) if you really want to properly secure your users. But it can be done and it should be done. And if it should be done, it should be done well.
It should actually be effective!
The modern approach to Security Awareness Training & Education (SATE) is failing, but that’s not just my opinion. The proof is in the numbers. We are spending more on cyber security than we ever have, yet we are seeing a record number of cyber incidents.
So how do we do this well? First, let’s talk about why the current model is failing.
Training & Educating the Right Way
The current SATE approach has disconnected everything the marketing folks have taught us about conditioning human behavior. At PeopleSec, we embrace what marketers have learned about human emotion and behavior and use those paradigms to develop training programs for our clients and their users.
If implemented properly, the following methodologies can have a significant impact on security and reduce user risk to nearly 0%.
1. High Frequency “Micro Training”
Due to the 144 character social media world in which we currently live, user training should be bite-sized and easy to digest. It’s often much more effective to provide 60 different one-minute training sessions throughout the year than just one annual 60-minute training session.
Because users have short attention spans and a tendency to relapse after learning, constant reminders are needed. Phishing threats evolve daily, not yearly, quarterly or even monthly, so proper user training should reflect the fast-paced nature of the threats we are trying to stop.
We must be constantly educating our users.
2. Measure Everything
If you can imagine it, you can measure it.
Another aspect we borrowed from our marketing friends is the importance of tracking, measuring and analyzing everything our client’s users do during training sessions (for example, phishing emulations).
The best SATE programs should have proper insight into user risk and this can’t be properly done without the right data. If you’re only trying to evaluate risk once per quarter or month, you’re not going to identify the risky users and are leaving gaps in your perimeter and your users become the low hanging fruit. Our system ranks all users as high, medium or low risk based on multiple metrics such as:
- Did the user open the phishes? Did the user open the educational emails?
- How long does it take for the user to relapse or forget their training?
- What was the cumulative risk of that user each month?
- How many months has the user spent as Low, Medium and High risk?
- What was the cumulative difficulty of the phishes sent during the attack emulation this month compared to the previous month?
- What type of phishes is the user most susceptible to?
The best decisions are made using the best data. If individual and collective user data is not there, you’re setting your enterprise up for failure.
3. User-Specific Training
SATE programs should customize training frequency, content and attack simulations to the individual needs of each user. For example, why should a SATE program waste the time of “low-risk” users by giving them training that’s intended only for “high-risk” users?
Alternatively, high-risk users tend to need so much education that the impact on human resources would be cost prohibitive without mass customization. So we train according to each user’s need and escalate training frequency and testing as needed.
It’s also important to change the tone of training materials based on user risk (higher risk = more aggressive). It makes sense to only send high difficulty phishes and spear phishes to your lowest risk users.
Using the data we collect (see #2 above), we can preemptively increase attack simulation and education frequency based on previously recorded metrics (such as user retention rate). Even if you can’t get down to the specific individual user, at least users can be classified into high, medium and low risk categories and customize training for those 3 groups.
4. Human Intervention
Technology can only drive user risk numbers to a certain low and, therefore, human intervention is required to drive numbers even lower. When it comes to changing individual user’s behavior, we’ve found that it’s typically better to use carrots rather than sticks.
Users need to feel like they are either part of the solution or part of the problem. Some employees only become receptive and participative AFTER a human being has talked to them. For example, a simple phone call can help to move a user from the high risk group to the low risk group.
Often it’s not even an employee’s fault. Sometimes it’s a business process that’s at the root of the problem. When we notice a particular department within a client’s organization that has a high level of susceptibility for a particular type of phish, this can often be traced back to a faulty business process. We can then address the cause using a focus group and remedy the vulnerability by encouraging the organization to change their business process.
Simple human interaction can increase the comfort zone of people, making them more apt to learn, change, and retain what they need. Why wouldn’t we take advantage of this and adjust our SATE training accordingly?
5. Timely Education
Programs that don’t capitalize on “Just in Time” education opportunities are missing a valuable time for education while the user is highly receptive (at the moment a mistake is realized). For example, if a user clicks on one of our phishing emulations, we often give instant feedback with a landing page announcement, immediate email notification, or phone call.
We want to make sure we prioritize education over exploitation. It’s often more effective to invoke an emotional response from the user. This helps solidify the training in their mind and produces a higher retention rate.
6. Entertaining & Engaging Content
Usually long content is, by default, boring. Lengthy content causes the user to lose interest and impersonal content causes users to not engage.
At PeopleSec, we limit the length of most of our training sessions to under 1 minute and we often use humor to help drive user retention. Again, if it works in marketing, we can make it work in security awareness education too.
7. High Frequency Attack Emulations
Programs that don’t conduct high frequency phishing attack emulations tend to have higher use relapse percentages. This leaves users susceptible to real world targeted attacks.
Increasing the frequency and number of phishing attack emulations against the user has the net benefit of obtaining key metrics and is the best way to truly understand risk.
Attack emulations should vary in difficulty and frequency, just like real life. They should include, spear phishing, complex general target phishes, and easily identifiable mass phishes (ie Nigerian style).
Get creative with these and be proactive with your training. If there is a specific phish hitting your industry, then conduct attack emulations of that exact threat before it happens. Users will be better prepared if/when they see it in the wild.
8. Create Competition
Social engineering attacks manipulate employee emotions to get what the attacker wants, so SATE programs should do likewise to get employees motivated to become more secure.
“Gamify” security training by creating a competition between departments and award the winning department with a catered lunch. You could even create a leaderboard and award the most secure users in the company.
Additionally, our training programs include emotional stimuli on phish emulation landing pages. We utilize “scareware” to help elicit an emotional response from the user. This includes things like green text on a black screen, changing the desktop background, and multiple pop ups that require the user to read each bubble (which contains security awareness education) and click “I agree” before they can regain use of their computer.
9. Create & Sustain Vigilance
No one is immune from making an occasional mistake now and then. Even InfoSec staff can get complacent when reading emails if, for example, they are struggling through a stressful situation at home (divorce, death in the family, etc).
To help stay vigilant, every organization should have a standard email signature and an alert at the top of every email that indicates if it’s an external or internal email. Give your users a clear way of knowing if an email is safe by including a secure passphrase or tagline. You might even use nicknames instead of real names when communicating with employees via email.
It’s important to create an easy avenue for users to report legitimate phishing attacks (and add that to your metrics too). Most security awareness programs today do not measure employee’s failure to report a legitimate phish.
PeopleSec Can Help
If you now realize that your organization’s users are vulnerable to phishing attacks and other cyber security threats; or you aren’t sure if you’re doing all you can to reduce user risk to nearly 0%, contact us today and we’ll be glad to assess your organization’s security risk.