9 Signs Your Security Awareness Training is Failing
/0 Comments/in Phishing, Security Awareness Training and Education (SATE) /by patrickIn this article, I’ll show you why the modern approach to Security Awareness Training & Education (SATE) is failing and explain how we can do it better.
Like most things that might initially seem impossible, it all begins with a proper mindset. There’s an old saying that goes something like this: “Whether you think you can, or you think you can’t, either way you’re right”.
But if this maxim proves true across all industries and cultures, why do we throw our hands up at the thought of properly training users and say “Well, you can’t patch stupid!”?
The only guaranteed way to fail is to say “I can’t”.
Addressing the User Problem
Experienced attackers know that if they want access to a “secure” network all they need to find is the low hanging fruit. An organization’s users often represent the lowest hanging fruit because targeting users allows an attacker to bypass almost ALL security controls. All the attacker has to do is inherit user privileges to gain access to the network and then they are free to cause as much damage as possible.
Enterprises are not properly addressing their user risk, and because of this, it’s a wide open gap in most security departments. Does your organization approach network security like this character from Lemony Snicket’s Series of Unfortunate Events?

If you don’t properly address your user problem, this is exactly what your security looks like. Attackers know that they can always bypass security controls by targeting the weakest link…your users. Even the most sophisticated digital security perimeter puts the attacker in the DMZ, but the attacker wants to be in the user land where the data resides and where the security controls are a lot less likely to catch said attacker.
The truth is that human error is the ultimate root cause of every cyber incident. So if we can do better with human decision-making, we can do better with security.
But how?
Investing in Your Users
The answer lies in investing in your users. But I’m willing to admit that securing users is not easy to implement. It takes a dedicated effort of time and money (or both) if you really want to properly secure your users. But it can be done and it should be done. And if it should be done, it should be done well.
It should actually be effective!
The modern approach to Security Awareness Training & Education (SATE) is failing, but that’s not just my opinion. The proof is in the numbers. We are spending more on cyber security than we ever have, yet we are seeing a record number of cyber incidents.
So how do we do this well? First, let’s talk about why the current model is failing.
Training & Educating the Right Way
The current SATE approach has disconnected everything the marketing folks have taught us about conditioning human behavior. At PeopleSec, we embrace what marketers have learned about human emotion and behavior and use those paradigms to develop training programs for our clients and their users.
If implemented properly, the following methodologies can have a significant impact on security and reduce user risk to nearly 0%.
1. High Frequency “Micro Training”
Due to the 144 character social media world in which we currently live, user training should be bite-sized and easy to digest. It’s often much more effective to provide 60 different one-minute training sessions throughout the year than just one annual 60-minute training session.
Because users have short attention spans and a tendency to relapse after learning, constant reminders are needed. Phishing threats evolve daily, not yearly, quarterly or even monthly, so proper user training should reflect the fast-paced nature of the threats we are trying to stop.
We must be constantly educating our users.
2. Measure Everything
If you can imagine it, you can measure it.
Another aspect we borrowed from our marketing friends is the importance of tracking, measuring and analyzing everything our client’s users do during training sessions (for example, phishing emulations).
The best SATE programs should have proper insight into user risk and this can’t be properly done without the right data. If you’re only trying to evaluate risk once per quarter or month, you’re not going to identify the risky users and are leaving gaps in your perimeter and your users become the low hanging fruit. Our system ranks all users as high, medium or low risk based on multiple metrics such as:
- Did the user open the phishes? Did the user open the educational emails?
- How long does it take for the user to relapse or forget their training?
- What was the cumulative risk of that user each month?
- How many months has the user spent as Low, Medium and High risk?
- What was the cumulative difficulty of the phishes sent during the attack emulation this month compared to the previous month?
- What type of phishes is the user most susceptible to?
The best decisions are made using the best data. If individual and collective user data is not there, you’re setting your enterprise up for failure.
3. User-Specific Training
SATE programs should customize training frequency, content and attack simulations to the individual needs of each user. For example, why should a SATE program waste the time of “low-risk” users by giving them training that’s intended only for “high-risk” users?
Alternatively, high-risk users tend to need so much education that the impact on human resources would be cost prohibitive without mass customization. So we train according to each user’s need and escalate training frequency and testing as needed.
It’s also important to change the tone of training materials based on user risk (higher risk = more aggressive). It makes sense to only send high difficulty phishes and spear phishes to your lowest risk users.
Using the data we collect (see #2 above), we can preemptively increase attack simulation and education frequency based on previously recorded metrics (such as user retention rate). Even if you can’t get down to the specific individual user, at least users can be classified into high, medium and low risk categories and customize training for those 3 groups.
4. Human Intervention
Technology can only drive user risk numbers to a certain low and, therefore, human intervention is required to drive numbers even lower. When it comes to changing individual user’s behavior, we’ve found that it’s typically better to use carrots rather than sticks.
Users need to feel like they are either part of the solution or part of the problem. Some employees only become receptive and participative AFTER a human being has talked to them. For example, a simple phone call can help to move a user from the high risk group to the low risk group.
Often it’s not even an employee’s fault. Sometimes it’s a business process that’s at the root of the problem. When we notice a particular department within a client’s organization that has a high level of susceptibility for a particular type of phish, this can often be traced back to a faulty business process. We can then address the cause using a focus group and remedy the vulnerability by encouraging the organization to change their business process.
Simple human interaction can increase the comfort zone of people, making them more apt to learn, change, and retain what they need. Why wouldn’t we take advantage of this and adjust our SATE training accordingly?
5. Timely Education
Programs that don’t capitalize on “Just in Time” education opportunities are missing a valuable time for education while the user is highly receptive (at the moment a mistake is realized). For example, if a user clicks on one of our phishing emulations, we often give instant feedback with a landing page announcement, immediate email notification, or phone call.
We want to make sure we prioritize education over exploitation. It’s often more effective to invoke an emotional response from the user. This helps solidify the training in their mind and produces a higher retention rate.
6. Entertaining & Engaging Content
Usually long content is, by default, boring. Lengthy content causes the user to lose interest and impersonal content causes users to not engage.
At PeopleSec, we limit the length of most of our training sessions to under 1 minute and we often use humor to help drive user retention. Again, if it works in marketing, we can make it work in security awareness education too.
7. High Frequency Attack Emulations
Programs that don’t conduct high frequency phishing attack emulations tend to have higher use relapse percentages. This leaves users susceptible to real world targeted attacks.
Increasing the frequency and number of phishing attack emulations against the user has the net benefit of obtaining key metrics and is the best way to truly understand risk.
Attack emulations should vary in difficulty and frequency, just like real life. They should include, spear phishing, complex general target phishes, and easily identifiable mass phishes (ie Nigerian style).
Get creative with these and be proactive with your training. If there is a specific phish hitting your industry, then conduct attack emulations of that exact threat before it happens. Users will be better prepared if/when they see it in the wild.
8. Create Competition
Social engineering attacks manipulate employee emotions to get what the attacker wants, so SATE programs should do likewise to get employees motivated to become more secure.
“Gamify” security training by creating a competition between departments and award the winning department with a catered lunch. You could even create a leaderboard and award the most secure users in the company.
Additionally, our training programs include emotional stimuli on phish emulation landing pages. We utilize “scareware” to help elicit an emotional response from the user. This includes things like green text on a black screen, changing the desktop background, and multiple pop ups that require the user to read each bubble (which contains security awareness education) and click “I agree” before they can regain use of their computer.
9. Create & Sustain Vigilance
No one is immune from making an occasional mistake now and then. Even InfoSec staff can get complacent when reading emails if, for example, they are struggling through a stressful situation at home (divorce, death in the family, etc).
To help stay vigilant, every organization should have a standard email signature and an alert at the top of every email that indicates if it’s an external or internal email. Give your users a clear way of knowing if an email is safe by including a secure passphrase or tagline. You might even use nicknames instead of real names when communicating with employees via email.
It’s important to create an easy avenue for users to report legitimate phishing attacks (and add that to your metrics too). Most security awareness programs today do not measure employee’s failure to report a legitimate phish.
PeopleSec Can Help
If you now realize that your organization’s users are vulnerable to phishing attacks and other cyber security threats; or you aren’t sure if you’re doing all you can to reduce user risk to nearly 0%, contact us today and we’ll be glad to assess your organization’s security risk.
Security Awareness – The Greatest Cyber Insanity
/0 Comments/in Phishing, Security Awareness Training and Education (SATE) /by patrickAwareness – The Greatest Cyber Insanity
One of the most common ways to help prevent cyber security breaches in enterprises is Cyber Security Awareness Training. Unfortunately training is often implemented poorly and inefficiently.
In this article, I’d like to talk about ten reasons why most cyber security training programs fail and what we can do to improve that.
We now know that the average breach detection time is over 90 days and that the number of cyber security breaches has only increased in recent years. Quite frankly, if it can be coded or programmed, it can certainly be hacked. No measure of security features can stop the best hackers so it’s more important now than ever to focus your time and budget on the one thing that matters most when it comes to preventing cyber security breaches…humans.
Technology is Not the Problem
Cyber security is not a technology problem, it’s a human problem. People are involved in every layer of the cyber security onion. Many hackers live by the notion of “Why attack the perimeter when you can attack the user?”.
When it comes to phishing, for example, antivirus software is in place to treat the symptom, but the problem lies in a person clicking on a phishing email. No amount of antivirus software can stop your employees from clicking on malicious email links when they shouldn’t.
Antivirus software only stops around 35% of viruses and has never even slowed our Ethical Hackers down. Wouldn’t it be better if we focused our energy and efforts on training employees to spot phish in the first place?
Money is Not the Problem
Most organizations spend around 5% of their cyber security budget on 90% of the problem. Cyber security tends to be very reactive, but a solution is needed to this problem right now. We who are in the industry have not been so good at future proofing our industry and we are treating symptoms rather than causes.
Enterprises are spending more and more money each year to help prevent cyber security incidents. Globally, it’s expected that cyber security spending will exceed $114 billion in 2018 alone.
Spending consistently increases about 10% year over year. It’s expected that total spending will exceed $1 trillion between 2017 and 2021. This includes products and services designed to prevent attacks as well as staff and personnel. These figures don’t even consider the money spent cleaning up in the aftermath of a breach.
We’re spending more yet doing worse.
Compliance is Not the Problem
Most enterprises see compliance as the finish line rather than the starting point. Their budgets are driven with the idea that compliance is the end goal, all while ignoring the risk that sits in front of them day after day.
In fact, according to 2018 Verizon DBIR, about 96% of security breaches start with a phish. It’s only when we focus more on the human problem with phishing rather than throwing more money at compliance and technology, that we can make strong progress toward a more secure infrastructure inside your enterprise.
We see this time and time again with our clients.
How Do We Fix This Problem?
Proper security awareness training is what we’ve found makes the most progress in helping prevent cyber security attacks inside enterprises.
Our approach is unique. We aim to educate – humans are like computers, hard to train but easy to program. Our training focuses more on programming your users to spot suspicious emails, for example, rather than conducting boring training seminars that no one enjoys.
The Four E’s of Security Awareness
- Entertaining – We must entertain our users to make them want to learn
- Encompassing – Does the program address all human security weaknesses
- Engaging – Users must be engaged in security monitoring and protection
- Effective – Programs need to be measured by results not compliance. For example, is it actually reducing the number of security incidents?
So let’s get in to the top 10 reasons typical security awareness training fails.
Top 10 Epic Security Awareness Fails
#10 – Under Qualified and Overworked Staff
Security staff tend to be overworked, under-qualified and they often don’t understand human psychology. Often, DIY programs are implemented but they get forgotten about and therefore are underutilized. The best DIY program in the world is only as good as how well and how often you use it. A tool sitting on a shelf, not being used, is worthless, no matter how useful the tool.
#9 – Poor User Engagement
Your users don’t care about cyber security because management doesn’t care about cyber security. If there is no security culture at your enterprise and no ramifications if an employee causes a breach, they won’t give a damn. Additionally, if there is no positive reinforcement for secure behavior, what incentive do your users have to stay vigilant?
#8 – Poor or Missing Data Collection
All of the security awareness training you conduct should be backed by and driven by specific data sets that are unique to your enterprise. You need to know things like how many phish clicks have occurred and what types of phishes your users are clicking on. It’s important to understand which employees are vulnerable and what level of risk (high, medium, low) they represent. How about relapse rate? That should also be tracked. If you can think of it, you need to measure it!
#7 – Poor Risk Insight
Proper data long with specific KPI’s should help you discover which employees pose the most risk, which departments and locations pose the most risk, who is/isn’t improving and so on. Special attention needs to be given to employees that have access to sensitive information, such as domain admins, HR, finance, etc.
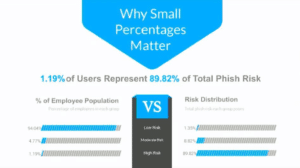
According to our own internal survey data, 1.19% of users represent 89.82% of the risk to any given enterprise. It’s the smallest percentage of users who expose the greatest risk.
#6 – Low Frequency Training
Security Awareness Training cannot be just an annual event. Lack of repetition is a very common cause for user relapse. Low frequency of training means your users are not keeping security front of mind and they’re not taking advantage of all the touch points. Cyber threats evolve daily – not yearly or quarterly or monthly. Additionally, infrequent training causes over complex messaging that causes employees to zone out and miss the importance of it altogether.
#5 – Boring Content
You can’t measure effectiveness of your training by the length of your training. Just because you have provided x number of hours of training, doesn’t mean that training has been effective. Content that is too lengthy and overly complex does not entertain and does not educate. It will intimidate your users and employees and sometimes it’s just downright painful to watch.
#4 – One Size Fits All Initiatives
A proper security awareness training program should adapt to individual user needs. Phishing exercises, for example, should adapt to individual user risk trends. Different people present different risks. Susan may be more susceptible to social media phishing attempts while Malik may be more prone to click on a malicious email about fantasy football. Not everyone needs the exact same training. Not everyone learns the same. One size fits all training is inefficient because different roles have different training needs.
#3 – Missing “Just In Time” (JIT) Engagement
The best feedback that occurs after a mistake is the feedback that occurs immediately after said mistake. Mistake realization anchors lessons in memory. The sooner you can give feedback, the better. We often accomplish this through follow up emails. If one of our client’s users succumbs to one of our phishing attempts, we’ll send an immediate email notifying them of their mishap. This helps condition the user to spot the phishing attempt the next time it lands in their inbox. Avoid overly complex landing pages and don’t forget about the human interaction. We’ve phone that a timely phone call is often the best strategy for helping correct high risk users.
#2 – Missing Emotional Anchoring
Emotional anchoring does many things. It increases retention, builds impact, pushes engagement and is scientifically proven. If you can evoke emotion (such as humor) as a part of your training programs, they will be more effective (science says so!).
#1 – Lousy human virus definitions
More phishing equals more human virus definitions which results in lower incident rates. Condition your users to watch for red flags by accompanying trending threats with simulations. The only fix for spear phishing is spear phishing emulations. Users are over 70% less likely to click on a phish if they see it first. We’ve identified 8 different types of phishing scams and if you’re only testing your users once per quarter, it could take up to 2 years to find out which types of phishes any single user is susceptible to.
Reduce the Risk
There’s no such thing as zero risk. Your cyber security awareness training should aim to reduce that risk to the lowest number possible. Would you let your 13 year old climb into a car with no training, license or permit? No, because they might kill themselves. Then why would you give employees access to computers without proper training? It could literally kill your business.
If you’d like more information on how PeopleSec can help your enterprise reduce the risk of a cyber intrusion, contact us today.
Social Media Safety
/0 Comments/in Security Awareness Training and Education (SATE), Social Engineering /by patrick
The Top 5 Social Media Threats ;
-
Hidden URLs
– These are quite common, often times leading to a site that then asks for login information.
-
Requests
– Someone may send you a warning or a request to take action or follow some link. Do not be fooled by these people, they will often try to manipulate emotions to get victims to react without thinking.
-
Fake online surveys and contests –
“Take this quiz to find out X!” These sort of posts on social media are effective bait to lure users into unsafe sites, where cyber criminals may install malware, spyware, or gather your information to misuse.
-
Fake customer service accounts –
Scammers on social media often pretend to represent legitimate organizations in order to steal sensitive information.
-
Live Streams
– Luring users to scammer ran websites with the promise of being able to view sports games, movies, etc…Once they have lured victims to their sites, they install malware, spyware, or get users to input credit card numbers. After all this they almost never even have the live stream they claimed to.
Security Awareness Training & Education Program, Crucial Elements to Incorporate
/0 Comments/in Security Awareness Training and Education (SATE) /by patrickDoes your organization take security awareness seriously? Would your employees be able to defend against social engineering attacks? Is the effectiveness of your organizational security frequently tested? You should be answering a resounding “Yes” to all of these questions. If you answer “no” or “I don’t know” this may be a sign that your organization has serious security vulnerabilities. The following is a high level overview of important elements in an effective security awareness training and education program.
Executive Support
This should be pretty obvious but is nevertheless quite important. When creating a security awareness program, you need to garner the support of C-Level decision makers. How can you gain their support? Simple. Most CISOs, CIOs, CTOs, etc.… are experienced in information security and already know that the vast majority of security breaches are due to human error. Furthermore, having a security awareness training and education program in place is often a legal requirement. So if you come to them with a solid plan, solving issues and making their life easier, they should (hopefully) be quite receptive. Now that you have the executives involved, employees lower down the chain will likely follow suit.
Establish a Security Awareness Baseline
Establish a baseline by staging phishing attacks (of various types), testing employee awareness. The metrics gained on each employee will not only help to identify who is putting your organization at risk but also quantify the success of your security awareness program over time. When conducting your baseline, it is important to stage attacks of varying difficulty (Nigerian, Spear, etc…)
Ongoing Training
Security awareness training and education is steadily moving away from the binge training of the past. The problem with binge training as we all know and have most likely experienced, is that we are forced to memorize questions and answers for a test once a year (or longer) and then slowly forget about it. Nowadays, organizations develop SATE (security awareness training and education) programs to be ongoing and therefore significantly more effective.
Make Training Relatable
Demonstrate to employees how poor security practices can lead to harm not only for the organization but also to themselves, by clearly articulating the risk associated with specific actions. Keep the training short and to the point, teach users by using emotion when possible. Security awareness training should incorporate phish from real life attacks. By doing this you will know that your employees can fend off what is currently being used to attack other organizations in your industry. When you hear about a real attack currently targeting your industry – launch that attack against your users first before the bad guys do. Remember if you aren’t attacking your users then only the bad guys are.
User Insight
Knowing specifically which individuals are putting your organization at risk is incredibly important. With this knowledge you will be able to give attention to the employees that need training and education the most, while minimizing disruption to those that behave securely. Furthermore, this metric can be of great value to management in decision making processes involving access and privileges. Any respectable Security Awareness Training and Education Program should at a minimum answer the following questions;
- Who are my high risk employees?
- Who are my most secure employees?
- Do I have any employees with high level access who are high risk?
Measure Everything
You will use this data to create two types of secure reports. One that is a concise overview, which C-Level executives often prefer. The second report should be a more in depth version that shows details of how each employee is performing in various areas. Examples of metrics to maintain for each user, which help to continuously improve your SATE program include;
- Retention
- Focus
- Engagement
- Risk
- Severity of Risk
- To What Types of Phish is Each User Most Susceptible
Customize
Ok, so this one is not absolutely necessary but is huge a plus if you can pull it off, with the metrics now in hand, the data can be used to enhance user learning significantly. Use metrics such as relapse frequency to indicate how often each employee should be training. User focus will tell you how long training should be and utilizing Phish Susceptibility Type can help you decide which type of phish will be most effective for training each employee.
Information Security Awareness Tips from a Newborn
/0 Comments/in Security Awareness Training and Education (SATE), Security Tips /by AlexWhile the linked post may be stretching a correlation, the points are accurate, entertaining, and what Information Security loving expert doesn’t want to buy that onesie. The top tip, Putting in only 45 minutes a year is bad, PeopleSec is in full agreement. A single 45-minute training a year is not a good practice.