Security Awareness – The Greatest Cyber Insanity
Awareness – The Greatest Cyber Insanity
One of the most common ways to help prevent cyber security breaches in enterprises is Cyber Security Awareness Training. Unfortunately training is often implemented poorly and inefficiently.
In this article, I’d like to talk about ten reasons why most cyber security training programs fail and what we can do to improve that.
We now know that the average breach detection time is over 90 days and that the number of cyber security breaches has only increased in recent years. Quite frankly, if it can be coded or programmed, it can certainly be hacked. No measure of security features can stop the best hackers so it’s more important now than ever to focus your time and budget on the one thing that matters most when it comes to preventing cyber security breaches…humans.
Technology is Not the Problem
Cyber security is not a technology problem, it’s a human problem. People are involved in every layer of the cyber security onion. Many hackers live by the notion of “Why attack the perimeter when you can attack the user?”.
When it comes to phishing, for example, antivirus software is in place to treat the symptom, but the problem lies in a person clicking on a phishing email. No amount of antivirus software can stop your employees from clicking on malicious email links when they shouldn’t.
Antivirus software only stops around 35% of viruses and has never even slowed our Ethical Hackers down. Wouldn’t it be better if we focused our energy and efforts on training employees to spot phish in the first place?
Money is Not the Problem
Most organizations spend around 5% of their cyber security budget on 90% of the problem. Cyber security tends to be very reactive, but a solution is needed to this problem right now. We who are in the industry have not been so good at future proofing our industry and we are treating symptoms rather than causes.
Enterprises are spending more and more money each year to help prevent cyber security incidents. Globally, it’s expected that cyber security spending will exceed $114 billion in 2018 alone.
Spending consistently increases about 10% year over year. It’s expected that total spending will exceed $1 trillion between 2017 and 2021. This includes products and services designed to prevent attacks as well as staff and personnel. These figures don’t even consider the money spent cleaning up in the aftermath of a breach.
We’re spending more yet doing worse.
Compliance is Not the Problem
Most enterprises see compliance as the finish line rather than the starting point. Their budgets are driven with the idea that compliance is the end goal, all while ignoring the risk that sits in front of them day after day.
In fact, according to 2018 Verizon DBIR, about 96% of security breaches start with a phish. It’s only when we focus more on the human problem with phishing rather than throwing more money at compliance and technology, that we can make strong progress toward a more secure infrastructure inside your enterprise.
We see this time and time again with our clients.
How Do We Fix This Problem?
Proper security awareness training is what we’ve found makes the most progress in helping prevent cyber security attacks inside enterprises.
Our approach is unique. We aim to educate – humans are like computers, hard to train but easy to program. Our training focuses more on programming your users to spot suspicious emails, for example, rather than conducting boring training seminars that no one enjoys.
The Four E’s of Security Awareness
- Entertaining – We must entertain our users to make them want to learn
- Encompassing – Does the program address all human security weaknesses
- Engaging – Users must be engaged in security monitoring and protection
- Effective – Programs need to be measured by results not compliance. For example, is it actually reducing the number of security incidents?
So let’s get in to the top 10 reasons typical security awareness training fails.
Top 10 Epic Security Awareness Fails
#10 – Under Qualified and Overworked Staff
Security staff tend to be overworked, under-qualified and they often don’t understand human psychology. Often, DIY programs are implemented but they get forgotten about and therefore are underutilized. The best DIY program in the world is only as good as how well and how often you use it. A tool sitting on a shelf, not being used, is worthless, no matter how useful the tool.
#9 – Poor User Engagement
Your users don’t care about cyber security because management doesn’t care about cyber security. If there is no security culture at your enterprise and no ramifications if an employee causes a breach, they won’t give a damn. Additionally, if there is no positive reinforcement for secure behavior, what incentive do your users have to stay vigilant?
#8 – Poor or Missing Data Collection
All of the security awareness training you conduct should be backed by and driven by specific data sets that are unique to your enterprise. You need to know things like how many phish clicks have occurred and what types of phishes your users are clicking on. It’s important to understand which employees are vulnerable and what level of risk (high, medium, low) they represent. How about relapse rate? That should also be tracked. If you can think of it, you need to measure it!
#7 – Poor Risk Insight
Proper data long with specific KPI’s should help you discover which employees pose the most risk, which departments and locations pose the most risk, who is/isn’t improving and so on. Special attention needs to be given to employees that have access to sensitive information, such as domain admins, HR, finance, etc.
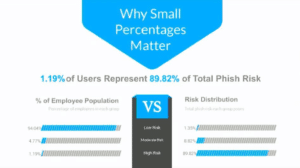
According to our own internal survey data, 1.19% of users represent 89.82% of the risk to any given enterprise. It’s the smallest percentage of users who expose the greatest risk.
#6 – Low Frequency Training
Security Awareness Training cannot be just an annual event. Lack of repetition is a very common cause for user relapse. Low frequency of training means your users are not keeping security front of mind and they’re not taking advantage of all the touch points. Cyber threats evolve daily – not yearly or quarterly or monthly. Additionally, infrequent training causes over complex messaging that causes employees to zone out and miss the importance of it altogether.
#5 – Boring Content
You can’t measure effectiveness of your training by the length of your training. Just because you have provided x number of hours of training, doesn’t mean that training has been effective. Content that is too lengthy and overly complex does not entertain and does not educate. It will intimidate your users and employees and sometimes it’s just downright painful to watch.
#4 – One Size Fits All Initiatives
A proper security awareness training program should adapt to individual user needs. Phishing exercises, for example, should adapt to individual user risk trends. Different people present different risks. Susan may be more susceptible to social media phishing attempts while Malik may be more prone to click on a malicious email about fantasy football. Not everyone needs the exact same training. Not everyone learns the same. One size fits all training is inefficient because different roles have different training needs.
#3 – Missing “Just In Time” (JIT) Engagement
The best feedback that occurs after a mistake is the feedback that occurs immediately after said mistake. Mistake realization anchors lessons in memory. The sooner you can give feedback, the better. We often accomplish this through follow up emails. If one of our client’s users succumbs to one of our phishing attempts, we’ll send an immediate email notifying them of their mishap. This helps condition the user to spot the phishing attempt the next time it lands in their inbox. Avoid overly complex landing pages and don’t forget about the human interaction. We’ve phone that a timely phone call is often the best strategy for helping correct high risk users.
#2 – Missing Emotional Anchoring
Emotional anchoring does many things. It increases retention, builds impact, pushes engagement and is scientifically proven. If you can evoke emotion (such as humor) as a part of your training programs, they will be more effective (science says so!).
#1 – Lousy human virus definitions
More phishing equals more human virus definitions which results in lower incident rates. Condition your users to watch for red flags by accompanying trending threats with simulations. The only fix for spear phishing is spear phishing emulations. Users are over 70% less likely to click on a phish if they see it first. We’ve identified 8 different types of phishing scams and if you’re only testing your users once per quarter, it could take up to 2 years to find out which types of phishes any single user is susceptible to.
Reduce the Risk
There’s no such thing as zero risk. Your cyber security awareness training should aim to reduce that risk to the lowest number possible. Would you let your 13 year old climb into a car with no training, license or permit? No, because they might kill themselves. Then why would you give employees access to computers without proper training? It could literally kill your business.
If you’d like more information on how PeopleSec can help your enterprise reduce the risk of a cyber intrusion, contact us today.




Leave a Reply
Want to join the discussion?Feel free to contribute!